Configuring SEAL Elastic Stack via Script¶
Elasticsearch uses different indices for the log, statistics, audit and accounting data of PLOSSYS Output Engine.
For easyPRIMA you only need to configure audit data in Kibana.
For SEAL Operator you only need to configure log and audit data in Kibana.
For the different indices you can configure the housekeeping in Elasticsearch (Index Lifecycle Management, ILM).
If you prefer to proceed manually in the Kibana user interface, you will find the step-by-step instructions in Configuring SEAL Elastic Stack by Hand .
The load-config Script¶
SEAL Elastic Stack provides the load-config script and several configuration files to create all necessary components for the housekeeping of the stored data of PLOSSYS Output Engine, PLOSSYS 4, SEAL Operator, PLOSSYS Distribution Engine/DPF, and easyPRIMA.
After the version update you have to start the load-config script again to update the configuration, too.
You will find the script in the following directory:
"C:\Program Files\SEAL Systems\seal-elasticstack-configuration\configuration\load-config.js"
You may use the load-config script in different operation modes:
-
Non-overwrite mode (default):
The
load-configscript checks, whether the specific index exists and adds only settings that are missing.This is the default.
-
Overwrite mode (set -o flag when calling the script):
The
load-configscript overwrites already existing workspaces and indices.Execute the script with the
-ooption.
Hint - overwriting independent of the operation mode
Independent of the operation mode, the load-config script
-
always overwrites
-
dashboard configurations to protect the consistency of the consecutive configurations
-
index templates
-
any non-customer-specific pipelines
For details on pipelines, see Configuring pipelines.
-
-
never overwrites
-
index lifecycle policies
-
any customer-specific pipelines.
Their names must contain the string
custom. They are only created, if not yet existing.If you wish to have them updated, you have to delete them manually in the Kibana user interface before you start the version update.
For details on pipelines, see Configuring pipelines.
-
Hint - usage
Execute the script with the -h or -help option to get the usage.
Executing the Script¶
-
Stop the
seal-filebeatservices on all PLOSSYS Output Engine, PLOSSYS 4, SEAL Operator, PLOSSYS Distribution Engine/DPF, and easyPRIMA servers to stop the data transfer to Elasticsearch:stop-service seal-filebeatstop-service seal-p4-accounting-filebeatstop-service seal-operator-filebeatstop-service seal-dpf-filebeat -
By default, the configuration matches the installation of PLOSSYS Output Engine, PLOSSYS 4, SEAL Operator, PLOSSYS Distribution Engine/DPF, and easyPRIMA. If you still need to modify the configuration, do this on the management server in the directory structure described in Configuring the Script below.
-
In a PowerShell (Administrator) on the management server, start the
load-configscript for PLOSSYS Output Engine:cd "C:\Program Files\SEAL Systems\seal-elasticstack-configuration" .\node\node.exe .\configuration\load-config.js -
Start the
load-configscript a second time for easyPRIMA, if required:cd "C:\Program Files\SEAL Systems\seal-elasticstack-configuration" .\node\node.exe .\configuration\load-config.js -c seal-easyprima -
Start the
load-configscript a third time for SEAL Operator, if required:cd "C:\Program Files\SEAL Systems\seal-elasticstack-configuration" .\node\node.exe .\configuration\load-config.js -c seal-operator -
Start the
load-configscript a fourth time for PLOSSYS Distribution Engine/DPF, if required:cd 'C:\Program Files\SEAL Systems\seal-elasticstack-configuration' .\node\node.exe .\configuration\load-config.js -c seal-dpf -
Start the
load-configscript once more to configure a common index pattern for SEAL, if you wish to combine audit log data of different sources:cd "C:\Program Files\SEAL Systems\seal-elasticstack-configuration" .\node\node.exe .\configuration\load-config.js -c seal-commonYou can also create a common index pattern for the audit indices manually, as described in Creating an Index Pattern for the Audit Indices.
-
Start the
seal-filebeatservices on all PLOSSYS Output Engine and management servers:start-service seal-filebeat -
Start the
seal-p4-accounting-filebeatservices on the PLOSSYS 4 server, if required:start-service seal-p4-accounting-filebeat -
Start the
seal-operator-filebeatservices on the SEAL Operator server, if required:start-service seal-operator-filebeat -
Start the
seal-dpf-filebeatservices on the PLOSSYS Distribution Engine/DPF server, if required:start-service seal-dpf-filebeat
Configuring the Script¶
The load-config script scans the directories stated below for JSON files and uses their content for the configuration of the different components of SEAL Elastic Stack.
If a JSON file or a subdirectory does not exist, the load-config script skips the configuration of the corresponding component:
"C:\Program Files\SEAL Systems\seal-elasticstack-configuration\configuration\<product_name>"
Example - configuration directory contained in SEAL Elastic Stack 7.16.0.53
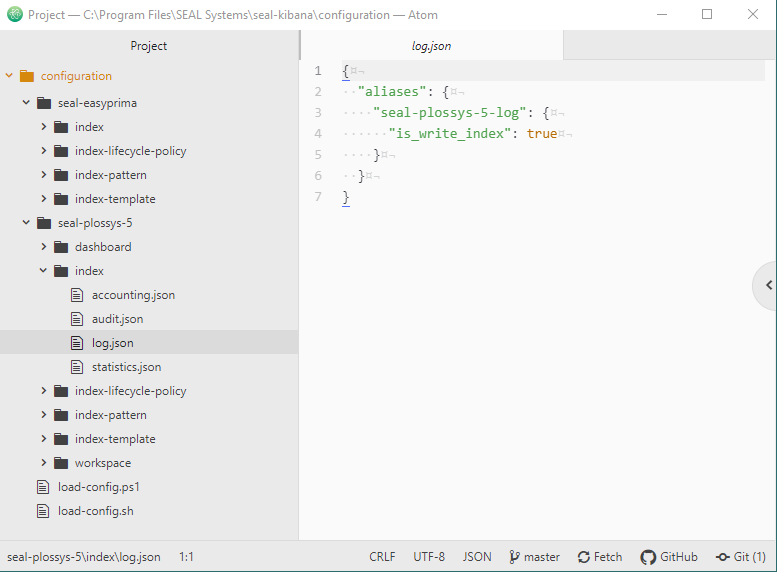
The subdirectories in the product-specific directories contain the JSON files for the different components:
-
index:Elasticsearch index
Literature
For details on the syntax, see original documentation.
-
index-lifecycle-policy:Housekeeping of the data in the specific index
Literature
For details on the syntax, see original documentation.
-
index-pattern:Index patterns for accessing the data stored in the specific index
Literature
For details on the syntax, see original documentation.
-
data-view:As of Elastic Stack 8.0
index-patternsare nameddata-viewsLiterature
For details on the syntax, see original documentation.
-
index-template:Template used when creating the index
Literature
For details on the syntax, see original documentation.
-
index-template/components:Reusable subcomponents for index templates
Literature
For details on the syntax, see original documentation.
The JSON files in the component-specific directories are named according to the data type that is to be configured:
-
accounting.json -
audit.json -
log.json -
statistics.json
The following subdirectory in the product-specific directories contains JSON files used to manipulate fields in index patterns:
-
fields:Customization of fields of an index pattern, for details on the syntax, see original documentation.
The following subdirectory in the product-specific directories contains JSON files that are used to define ingest pipelines:
-
pipelines:Ingest pipelines to adjust incoming data, for details on the syntax, see original documentation.
In Elasticsearch, you will find a number of predefined processors for ingest pipelines, which are comparable to filebeat processors. For details on this, see original documentation.
SEAL Elastic Stack 7.17.3 provides a concept for safely updating ingest pipelines. Aim is to combine SEAL-specific and customer-specific pipelines in a way that allows the SEAL-pipelines to be updated without overwriting the customer-specific parts.
Mit dieser Version 7.17.3 wird ein Konzept für Update-sichere Pipelines umgesetzt. Das Ziel ist, SEAL-spezifische und Customerspezifische Pipelines so zu kombinieren, dass bei einem Update die SEAL-Pipelines aktualisiert werden können, ohne die Kundenanteile zu überschreiben.
The following subdirectory in the product-specific directories contains JSON files used to adjust sample dashboards of Kibana:
-
dashboard:Dashboards to visualize the log data of PLOSSYS Output Engine, for details on the syntax, see original documentation.
The following subdirectory in the product-specific directories contains JSON files used to customize sample Kibana searches:
-
search:Predefined searches for an easier analyzation of the log data, for details on the syntax, see original documentation.
The following subdirectories in the product-specific directories contain JSON files that are used to customize the Kibana UI:
-
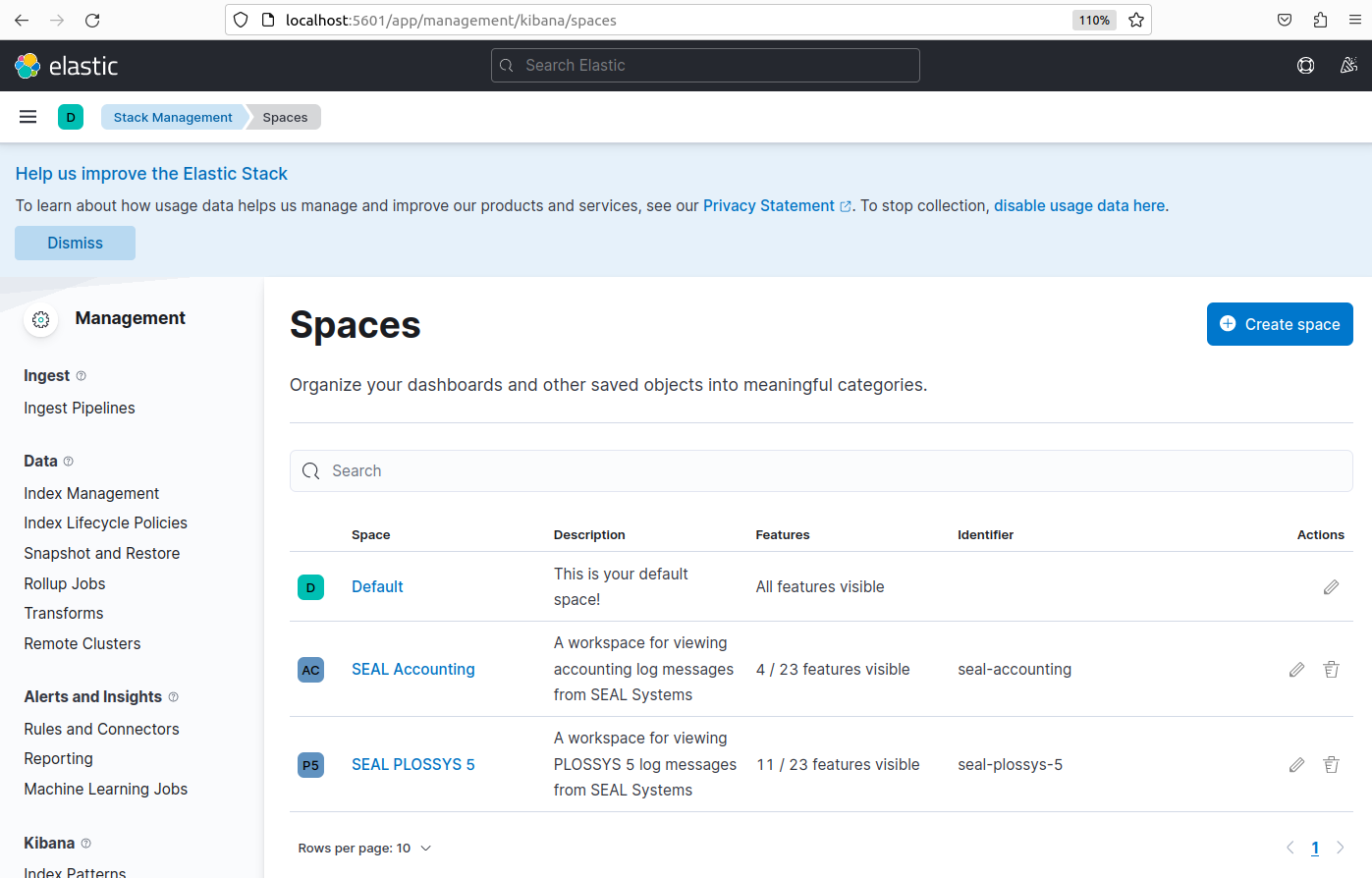
workspace:You can use Kibana spaces to restrict the Kibana user interface to essential features, e. g. a space for working with accounting data. In the screenshot, you can see that for the
SEAL Accountingspace only 4 of 23 possible features are visible. you will find a deactivated sample configuration for this space in the following directory:seal-elasticstack-configuration/configuration/seal-plossys-5/workspace/seal-accounting.json.example.Best practice here is combining a Kibana space with the definition of a corresponding role and its link, e. g. with an accounting user. For details on the syntax, see original documentation.
-
copy-saved-objects:When using Kibana spaces, you have 2 possibilities to set up kibana objects, like index patterns or dashboards:
- Create the kibana objects by using the `-workspace` option of the configuration script. - Copy the kibana objects by specifying a copy statement according to the Elastic API. For details on this, see [original documentation](https://www.elastic.co/guide/en/kibana/current/spaces-api-copy-saved-objects.html). In this directory, you can create a JSON file for each copy statement.
Example - using different spaces
The following subdirectories in the product-specific directories contain JSON files that are used to automatically generate users, roles, and role mappings. The directories currently contain *.json.example files as possible examples:
-
security/role:Definition of roles, for details on the syntax, see original documentation.
-
security/user:Definition of users, for details on the syntax, see original documentation.
You may use an online tool for creating passwords encrypted with BCRYPT10, which is the standard of Elasticsearch, e.g. Bcrypt Hash Generator & Verifier.
-
security/role-mapping:Definition of role mappings, for details on the syntax, see original documentation.
Backup Files¶
Before changing existing settings, the load-config script saves the corresponding original files in the following directory:
"C:\Program Files\SEAL Systems\seal-elasticstack-configuration\configuration\tmp\backup"
Log File of the Script¶
The load-config script logs its own error messages in a log file in the following directory:
"C:\Program Files\SEAL Systems\seal-elasticstack-configuration\configuration\tmp\log"
Indices for PLOSSYS Output Engine¶
In some cases you need to adjust PLOSSYS Output Engine environment variables, e. g. if you use a Kibana workspace.
In the PLOSSYS Output Engine system, the indices used in Elasticsearch for the log and statistics data of PLOSSYS Output Engine are specified in the following keys:
-
ELASTICSEARCH_INDEX_LOG -
ELASTICSEARCH_INDEX_STATISTICS
For details on the environment variables, refer to PLOSSYS Output Engine.